With the growing concerns of online privacy and security, encryption stands as one of your only defenses against bad actors on the lookout for your conversations. This is exaggerated by the fact that most self-hosted or affordable email solutions cut costs by skipping security.
These services either store email messages in plain text after delivery, skip encryption altogether, or use weak encryption practices that give you a false sense of security while leaving the system itself vulnerable to data and privacy breaches.
Fortunately, for users who have a Microsoft 365 Family or Personal subscription, Outlook.com has introduced strong encryption features that bypass the recipient’s lax security measures. Giving you the ability to send confidential and personal emails knowing that your messages stay encrypted during and after delivery.
Here’s the table of contents of this blog:
- How does Email Encryption in Outlook Work?
- How do I send an encrypted email message?
- How will readers view the encrypted message?
- Limitations of Email Encryption in Outlook
So let’s start!
How does Email Encryption in Outlook Work?
There are two methods of email encryption and security used by Outlook:
- Opportunistic TLS
- Email Encryption using Microsoft 365
By default, Outlook uses opportunistic TLS (Transport Layer Security) to send your emails to a recipient. It is a protocol used by Outlook as well as many other email service providers to encrypt emails during transit.
Opportunistic TLS starts with the highest level of security available and automatically downgrades to lower levels if the recipient’s email server does not support higher standards. While it makes email transmission more secure than not using any encryption at all, it does have its vulnerabilities.
Problems with Opportunistic TLS
Here is a quick summary of the problems with opportunistic TLS:
- Fallback to Unencrypted: If the recipient’s server does not support TLS, Outlook will send the email without any encryption, making it vulnerable to interception and eavesdropping.
- Transit-Only Encryption: Opportunistic TLS only encrypts the email in transit. Once the email reaches the recipient’s server, which could store it unencrypted, leaving it vulnerable to breaches if the server is compromised.
- Downgrade Attacks: Attackers can potentially interfere with the negotiation process between servers, forcing them to use the lowest level of encryption or none at all, making the emails easier to intercept.
- No Guarantee of Encryption: Since opportunistic TLS automatically adjusts to the recipient server’s capabilities, there is no guarantee that the email will remain encrypted throughout its entire journey as the recipient server might simply route it through another unencrypted network.
In short, Opportunistic TLS lets you match whatever security measures your recipients have implemented. In case there are no such measures, Outlook will send the email unencrypted, which bad actors can easily intercept to read its contents.
Email Encryption in Outlook using Microsoft 365
Advanced email encryption methods are available to those with a Microsoft 365 Family or Personal subscription. Users with an active subscription can use these to further strengthen their email security, ensuring that only the intended recipient can access the contents of their messages.
There are two core options available to Outlook.com users with an active Microsoft 365 subscription:
- Encrypt
- Do Not Forward
Encrypt
Traditional email encryption only works during transit, this option fixes that problem by not sending the original message at all.
Outlook ensures that your email remains secure during delivery as well as afterwards. Keeping it safe from interception and ensuring that the recipient does not store it in a readable form regardless of their security measures.
Do Not Forward
If you want to ensure that your recipients keep the contents of your email private, this option acts as an additional layer of deterrence in your favor.
Ideal in cases where you need to send confidential files over email, this option will automatically encrypt documents from the Microsoft Office Suite even after the recipients download them. Ensuring that your recipients cannot forward the downloaded files.
Keep in mind that this post-downloading encryption only works with files that are a part of the Microsoft Office suite, any third-party files, images, or PDFs will not have such protection.
How do I send an encrypted email message?
You will need an active Microsoft 365 Personal or Family subscription to send encrypted messages through Outlook. Users can choose either of the above encryption options when writing an email for the first time, here is what you need to do:
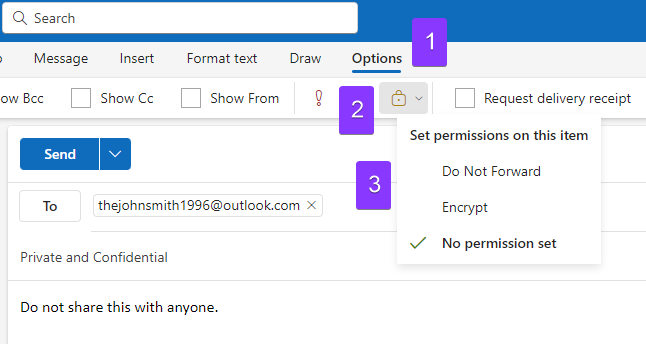
- Start drafting your email.
- Click on “Options” from the above menu to open the email-specific options.
- Click on the “Lock” Icon to open a dropdown menu with item permissions.
- Select either “Do Not Forward” or “Encrypt” from this menu depending on your preferences.
- Complete your email as you usually would and send it.
 Outlook will now leverage their integration with the Microsoft 365 ecosystem to encrypt the contents of your email as well as your attachments, depending on which encryption method you selected.
Outlook will now leverage their integration with the Microsoft 365 ecosystem to encrypt the contents of your email as well as your attachments, depending on which encryption method you selected.
How will readers view the encrypted message?
Encrypted emails for Outlook behave differently based on your recipient’s email client.
Outlook users will find no difference in experience as the client itself is capable of decrypting the message and confirming the recipient’s identity in the process. They will be able to read and reply to an encrypted email just like any other non-encrypted email.
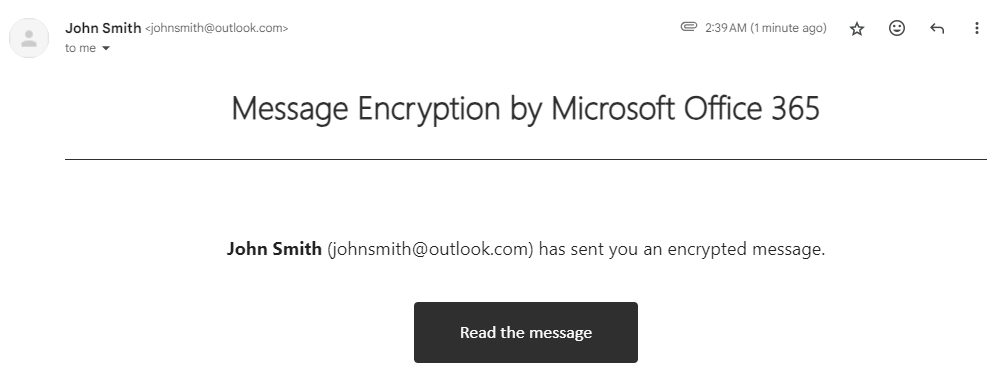
Recipients outside of Microsoft’s digital ecosystem will need to verify their identity, they can do so using two methods:
- Google & Yahoo Recipients can verify their identity by logging in with their respective accounts, the encrypted message will then open in a web browser where they can view it and download any attachments.
- Users of other email services will need to request a passcode to view the decrypted messages. Microsoft will send this passcode to the same email address that received the original encrypted message.
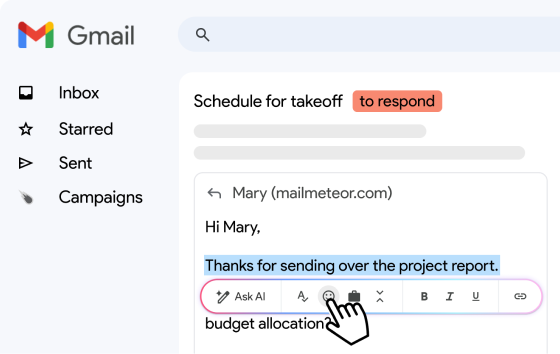
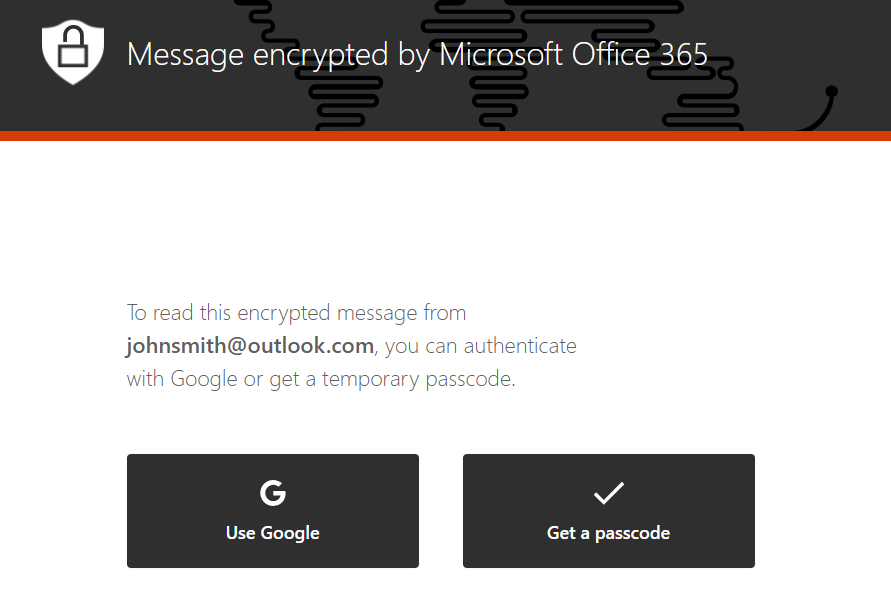 The above images show what a Gmail recipient will see upon opening a message encrypted through Outlook. They can either authenticate directly through their Google account or receive a passcode to the same email address that was originally meant to receive the encrypted message.
The above images show what a Gmail recipient will see upon opening a message encrypted through Outlook. They can either authenticate directly through their Google account or receive a passcode to the same email address that was originally meant to receive the encrypted message.
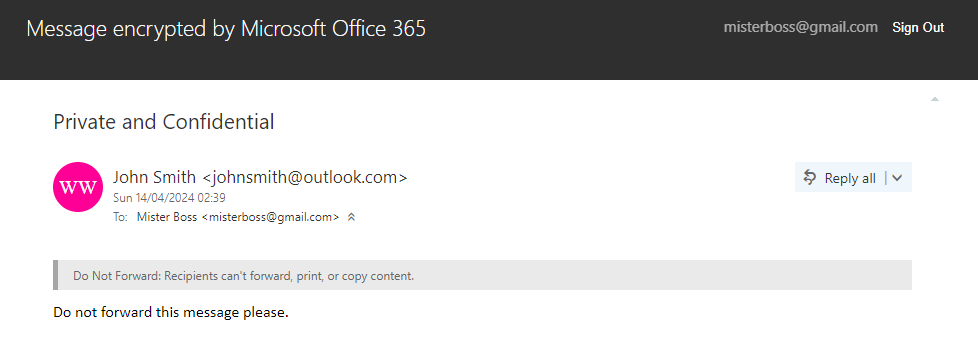
And finally, they will be able to view the message after authenticating themselves through either of the two options. But in both cases, they will need to leave their email client and the encrypted message will open in a new browser window.
Limitations of Email Encryption in Outlook
While Outlook’s email encryption does provide a decent level of security for messages sent through its platform, it is important for you to recognize their limitations, particularly on the recipient’s end. The biggest limitation is the fact that recipients who do not use Outlook must go through additional steps in order to view your message, but let us discuss the more technical limitations in front of us:
Recipient’s Mailbox Access
All of the security measures discussed above assume that the recipient’s mailbox is secure. In which case, we would not need the encryption functionality in the first place.
If a bad actor gains access to the recipient’s mailbox, they could potentially read encrypted messages as Microsoft sends a passcode to the same mailbox that received the encrypted message in order to verify the recipient’s identity.
So, someone with access to the stored plain text email messages can simply request a passcode and view the encrypted message anyway since they will be able to see the passcode.
Social Engineering
No encryption methods, including Outlooks, can mitigate the risks associated with human error or social engineering attacks.
If the recipient intentionally or knowingly shares their login credentials, the passcode, or falls victim to phishing attempts, an attacker could easily gain access to encrypted messages and attachments regardless of your security implementations.
(Please) Do Not Forward
Features like “Do Not Forward” can prevent recipients from sharing sensitive information directly, but it does not guarantee compliance.
Recipients can easily find ways to circumvent these restrictions. They can take screenshots, simply open the message in front of someone else, or just share their passcode instead. You should think of the Do Not Forward feature as a suggestion, as a means to inform the other person that you would not approve of them forwarding the message.
They can still do so without your knowledge.
So, What Should You Do?
While Outlook’s email encryption features offer a decent improvement in security, it is important for you to consider the hurdles that you will be placing in front of your recipients.
- Users within the Microsoft 365 ecosystem who use Outlook.com or the Outlook desktop app will have no trouble reading your encrypted messages.
- Recipients with a different email service provider will find it tedious to read and respond to your emails. Yahoo and Gmail users can save a few seconds by logging in with their accounts, but users with services like AOL, ProtonMail, or any other email client, will find it to be a meaningless requirement.
No encryption method can fully safeguard against human error, social engineering attacks, or a breach in mailbox security. The Microsoft 365 Email Encryption provides a valuable layer of protection, but it should just be one component on top of a deeper understanding of online privacy and security.